onlyread
nkctf only_read(ret2dlresolve)
很久以前学习过32位的ret2dlresolve,然后也没用过,做这道题是已经完全忘干净了,于是又花了一段时间重新学了一遍,这个题是64位的。ret2dlresolve一般适用于不能泄露libc地址的题目,本次把32位和64位一起大体学了一遍,一般是32位会用到栈迁移。这题我是跟着wp和其他师傅对ret2dlresolve讲解的文章做的。
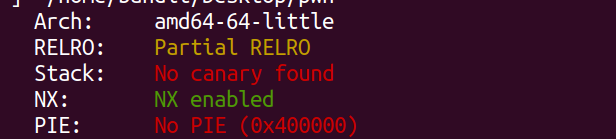
保护检查
源码分析
main函数
1 | int __cdecl main(int argc, const char **argv, const char **envp) |
前面有4个地方需要绕过才能进入可以溢出的next函数,都是base64加密
next函数
1 | ssize_t next() |
很明显的溢出
这里摘取师傅的引用的源码
1 | _dl_fixup (struct link_map *l, ElfW(Word) reloc_arg) // 第一个参数link_map,也就是got[1] |
exp
1 | from pwn import * |